
The environment plays a significant role to support life on earth. But there are some issues that are causing damages to life and the ecosystem of the earth. It is related to the not only environment but with everyone that lives on the planet. Besides, its main source is pollution, global warming, greenhouse gas, and many others. The everyday activities of human are constantly degrading the quality of the environment which ultimately results in the loss of survival condition from the earth.There are hundreds of issue that causing damage to the environment. But in this, we are going to discuss the main causes of environmental issues because they are very dangerous to life and the ecosystem.
Pollution – It is one of the main causes of an environmental issue because it poisons the air, water, soil, and noise. As we know that in the past few decades the numbers of industries have rapidly increased. Moreover, these industries discharge their untreated waste into the water bodies, on soil, and in air. Most of these wastes contain harmful and poisonous materials that spread very easily because of the movement of water bodies and wind. Greenhouse Gases – These are the gases which are responsible for the increase in the temperature of the earth surface. This gases directly relates to air pollution because of the pollution produced by the vehicle and factories which contains a toxic chemical that harms the life and environment of earth. Climate Changes – Due to environmental issue the climate is changing rapidly and things like smog, acid rains are getting common. Also, the number of natural calamities is also increasing and almost every year there is flood, famine, drought, landslides, earthquakes, and many more calamities are increasing.

Development recognises that social, economic and environmental issues are interconnected, and that decisions must incorporate each of these aspects if there are to be good decisions in the longer term.For sustainable development, accurate environment forecasts and warnings with effective information on pollution which are essential for planning and for ensuring safe and environmentally sound socio-economic activities should be made known.
THE EARTH IS WHAT WE
ALL HAVE IN COMMAN






































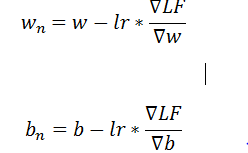






















































You must be logged in to post a comment.